The Null Device
Posts matching tags 'steganography'
2010/8/26
danah boyd has a new blog post on social steganography, or ways of encoding double meanings in messages one knows will be overheard.
Social steganography is one privacy tactic teens take when engaging in semi-public forums like Facebook. While adults have worked diligently to exclude people through privacy settings, many teenagers have been unable to exclude certain classes of adults – namely their parents – for quite some time. For this reason, they’ve had to develop new techniques to speak to their friends fully aware that their parents are overhearing. Social steganography is one of the most common techniques that teens employ. They do this because they care about privacy, they care about misinterpretation, they care about segmented communications strategies. And they know that technical tools for restricting access don’t trump parental demands to gain access. So they find new ways of getting around limitations. And, in doing so, reconstruct age-old practices.Often these techniques depend on shared cultural references; the fact that one's peers (typically within one's generation) have a shared vocabulary of song/movie/videogame/TV/&c. references has the convenient side-effect of providing a cryptolect that is all but parent-proof. (Which is why teens, i.e. those living in the totalitarian surveillance state of being a minor, are into ostensibly lame stuff like Justin Bieber and Fall Out Boy; few 'rents, even (or especially) those hip enough to know all about Joy Division and the Velvet Underground and krautrock and britpop and whatever, are going to study up on the latest godawful racket the kids these days are listening to just to be able to decode chatter most of which is going to be fairly inconsequential social administrivia. From which it might follow to say that when nostalgic adults listen to music from their adolescence, they are, knowingly or otherwise, revisiting the paraphernalia of strategies for mitigating a lack of freedom.) Anyway, boyd cites an example:
When Carmen broke up with her boyfriend, she “wasn’t in the happiest state.” The breakup happened while she was on a school trip and her mother was already nervous. Initially, Carmen was going to mark the breakup with lyrics from a song that she had been listening to, but then she realized that the lyrics were quite depressing and worried that if her mom read them, she’d “have a heart attack and think that something is wrong.” She decided not to post the lyrics. Instead, she posted lyrics from Monty Python’s “Always Look on the Bright Side of Life.” This strategy was effective. Her mother wrote her a note saying that she seemed happy which made her laugh. But her closest friends knew that this song appears in the movie when the characters are about to be killed. They reached out to her immediately to see how she was really feeling.It's debatable whether Monty Python counts as a parent-proof youth-culture reference. I'm guessing that the example story happened somewhere in the US, where Monty Python still has an aura of counterculture about it, and is likely to not be picked up by one's straight-laced 'rents. (Perhaps it happened in a devoutly Christian community, where The Life Of Brian would be virtually punk rock?)
Of course, nowadays Carmen could just have posted the update to Facebook under a filter, excluding her mother from seeing it, and her mother would have been none the wiser. (Unless Facebook has mechanisms preventing minors from hiding content from their parents, which I hadn't heard of.)
2010/4/29
Italian prosecutors have shut down a radio station after discovering that it was sending coded messages to Mafiosi via record requests:
Police listening in on a conversation between Pesce and his wife at Palmi jail in southern Italy heard him talking about record requests and concluded there was more to it than a love of music. According to a transcript leaked to the daily Il Giornale, Pesce told his wife, after scribbling down the name of a tune: "If it's positive you send me [this] song on the radio tonight. If it's negative you send me another."
2010/3/28
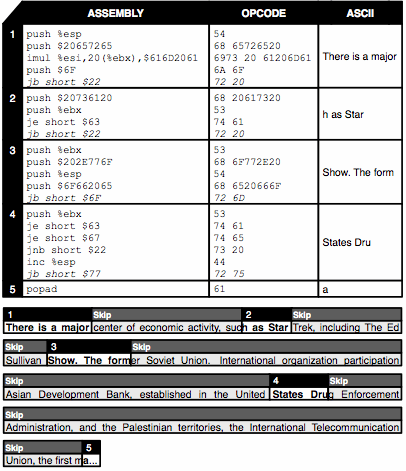
Security researchers are now working on ways of generating machine code that looks like English-language text (PDF).
In this paper we revisit the assumption that shellcode need be fundamentally different in structure than non-executable data. Specifically, we elucidate how one can use natural language generation techniques to produce shellcode that is superficially similar to English prose. We argue that this new development poses significant challenges for inline payloadbased inspection (and emulation) as a defensive measure, and also highlights the need for designing more efficient techniques for preventing shellcode injection attacks altogether.The code is generated by a language engine which selects fragments of text, Markov-chain-fashion, from a large source (such as Wikipedia or the Gutenberg Project). It looks like the random gibberish spammers pad their emails out with, though if executed, functions as x86 machine code. (Rather inefficient machine code, with a lot of jumps and circumlocutions to fit the constraints of looking like English, but good enough to sneak exploits through in.) Below is an example of some code thus disguised:
2007/6/15
Apparently the Mafia used a radio station in Naples to send instructions to hitmen encoded in song requests.
2005/8/11
In 2003, the CIA found what it thought were al-Qaeda terrorist instructions encoded in the al-Jazeera news ticker. The "instructions" detected by the CIA's steganalysis software included dates, flight numbers and the coordinates of targets including the White House and the small town of Tappahannock, Virginia, and resulted in the national terror alert level being raised from "extra-severe" to "brown trouser time" and almost 30 flights being cancelled. That is, until it emerged that the "hidden messages" were just the result of random noise, coincidence and the human pattern-finding instinct:
The problem with hunting messages hidden by steganography is that there are so few of them, any computer program will come up with false positives - messages that aren't really there. "The false positive rate, even if it's vanishingly small, starts to throw signals at you that makes you want to believe you're seeing messages. And somebody could be fooled by that if they didn't understand the nature of steganography," says Honeyman.This happened some time after it was discovered that al-Qaeda weren't hiding terrorist instructions in images on internet porn sites.
2004/4/9
Via Slashdot, an intriguing PowerPoint presentation (PDF) analysing spam, and using techniques to determine its origins. Among other claims it makes, spam intended to sell things is in the minority, and a lot of spam consists of other spammers' ads, resent to either identify valid recipients or to act as a carrier for encrypted messages between IRC groups. (It doesn't say anything about al-Qaeda terrorist cells or the like, but one imagines that if someone want to send coded instructions to covert operatives without disclosing their locations to traffic analysis, this would be a hell of a lot less conspicuous than mailing a Hotmail address accessed from a net café in Baluchistan or someplace.)
2003/8/26
Gibson's law applied to blackmail: Dutch blackmailer uses steganography to cover tracks, instructing victim to post bank card info encoded in a photograph in a fake car ad on an auction site. He then accessed the site through a US-based anonymiser. Mind you, the fact that the FBI nailed him in 24 hours nonetheless is somewhat thought-provoking. (via Techdirt)
2003/2/13
A Valentine's Day card has caused a homeland security alert in Pittsburgh; the man who bought the card for his daughter noticed that it contained the word "Jihad", and the message "It's Time To Be Mine". Could Osama bin Laden be using Valentine's Day cards to communicate with his sleeper agents?
2001/2/7
Those wily, inscrutable Arab terrorists are up to no good again; this time they're hiding terrorist attack plans in Internet porn and chat rooms. Or so say unnamed "U.S. officials and experts". Though for all we know the officials in question may be Bible-bashing anti-porn zealots in Bush's cabinet or some aspiring J. Edgar Hoover seeking to justify sweeping surveillance powers. (via Robot Wisdom)